Disable SSLV2, SSL 3 & Weak SSL Ciphers on IIS, Enable TLS 1.2
Need More than 50 Licenses? Please Request a Quote
Requires .NET Framework 2.0 or Greater, Windows Server
Check Your Server:
"It's a no brainer. The product just saved me time, money and a big headache."
Gerald T. - Sacramento State University
Have you disabled weak ciphers and protocols on your Microsoft Internet Information Server (IIS)? Weak SSL Protocols Ciphers are often enabled by default on Microsoft IIS servers. If you accept credit cards on your site, chances are you must comply with PCI which states that you must only allow Strong cryptography and security protocols.
PCI DSS Question 4.1 Are strong cryptography and security protocols, such as SSLTLS, SSH or IPSEC, used to safeguard sensitive cardholder data during transmission over open, public networks
PCI DSS Question 4.1 (c) Are security protocols implemented to use only secure configurations, and not support insecure versions or configurations?
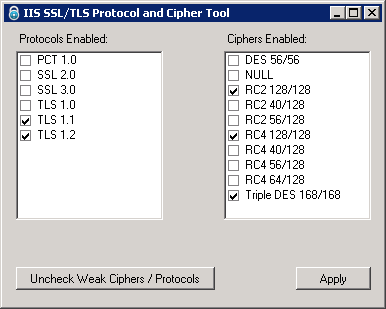
For Example on a Windows 2003 or 2008 Server the following protocols will be enabled by default:
- PCT 1.0
- SSL 2.0
- SSL 3.0
- TLS 1.0
The following Ciphers may be enabled on Windows 2003 or 2008 by default:
- DES 56/56
- RC2 128/128
- RC2 40/128
- RC4 128/128
- RC4 40/128
- RC4 56/128
- Triple DES 168/168
You must disable weak ciphers that use 40 bit keys (such as RC2 40/128 and RC4 40/128), or 56 bit keys (such as DES 56/56 or RC4 56/128), you should require key length of at least 128 bits.
Frequently Asked Questions about Disabling SSL Protocols & Ciphers
Will I loose customers by rejecting HTTPS connections with SSL v2, PCT 1.0, and 40 or 56 bit keys?
The chances of a customers browser not supporting strong cryptography is very small these days. All Modern browsers (IE7+, Firefox, Google Chrome, Opera) do not even ship with SSLv2 enabled.
Because todays merchant standards require strong cryptography, for online credit card transactions the potential customer would not be able to do business on most ecommerce sites.
Which SSL Protocols are Considered Weak, and should be disabled?
The PCT 1.0 and SSL 2.0 are considered weak. When you click the Uncheck Weak Ciphers / Protocols button in our IIS SSL Cipher tool these protocols will be unchecked.
As of October 2014, the SSL3 protocol is also considered weak, due to the POODLE vulnerability (CVE-2014-3566). Disabling SSLv3 may impact older HTTPS clients, such as IE6 on Windows XP. When you click the Uncheck Weak Ciphers / Protocols the SSLv3 protocol is NOT unchecked, you must do this manually if you wish to disable SSLv3.
Which Ciphers are Considered Weak, and should be disabled?
The ciphers DES 56/56, NULL, RC2 40/128, RC4 40/128, and RC4 56/128 are considered weak. When you click the Uncheck Weak Ciphers / Protocols button in our IIS SSL Cipher tool these ciphers will be unchecked.
What versions of IIS do I need to run this tool on?
As of this writing all versions of IIS 3 - 8, require a change in default SSL and TLS protocol support, future versions may require this as well.
What versions of windows are supported?
Because this tool is built with the .NET framework it can run on any version of Windows as long as you have the .NET Framework (2.0 or greater) installed. You can obtain the latest version here.
Does this EXE work on 32 / 64 bit servers?
Yes, both.
Does it work on Windows 2012 with IIS 8?
Yes, it works on Windows 2012 Servers running IIS 8. Windows 2012 enables TLS 1.1 and TLS 1.2 by default, but it also enables SSL 3.0 and TLS 1.0. You can use this tool to disable SSL and TLS protocols as needed.
Can I enable TLS 1.1 or TLS 1.2 on Windows 2008 R2 with this app?
Yes - TLS 1.1 and TLS 1.2 are not enabled by default on Windows 2008r2, but you can use this app to enable or disable these protocols.
Does it work on Windows 2008 with IIS 7?
Yes, it works on Windows 2008 Servers running IIS 7 or Windows 2008r2 servers running IIS 7.5.
Note that Windows 2008 and lower do not support TLS 1.1 or TLS 1.2. Windows 2008 R2 does support TLS 1.1 and TLS 1.2 protocols but they are disabled by default, you can use this tool to enable TLS 1.2 and TLS 1.1 on Windows 2008r2.
What about Windows 2003 with IIS 6?
Yes, it works on Windows 2003 as well as earlier versions of Windows and IIS. However these operating systems do not support TLS 1.1 and TLS 1.2, upgrade to Windows 2008r2 or greater.
My Security Scanning Company Said ... will this program help fix my problem?
Here are some common things your security company might say:
- Web Server supports weak SSL encryption certificates
- SSL Server supports weak encryption vulnerability
- The remote service supports the use of weak ssl ciphers
- Weak Supported SSL ciphers suites IIS
- SSL Weak Cipher Suites Supported
- Web Server supports outdated sslv2 protocol
- The remote service supports the use of medium strength SSL ciphers
- The remote service encrypts traffic using a protocol with known weaknesses.
- The remote host supports the use of SSL ciphers that offer either weak encryption or no encryption at all.
- The remote service supports the use of weak SSL ciphers. Description : The remote host supports the use of SSL ciphers that offer either weak encryption or no encryption at all. Solution: Reconfigure the affected application if possible to avoid use of weak ciphers.
- The remote service supports the use of medium strength SSL ciphers. Description : The remote host supports the use of SSL ciphers that offer medium strength encryption, which we currently regard as those with key lengths at least 56 bits and less than 112 bits. Solution: Reconfigure the affected application if possible to avoid use of medium strength ciphers.
- The remote service encrypts traffic using a protocol with known weaknesses. Description : The remote service accepts connections encrypted using SSL 2.0, which reportedly suffers from several cryptographic flaws and has been deprecated for several years. An attacker may be able to exploit these is s ues to conduct man-in-the-middle attacks or decrypt communications between the affected service and clients. Solution: Consult the application's documentation to disable SSL 2.0 and use SSL 3.0 or TLS 1.0 instead.
- Encrypted with obsolete cryptography
If your security company is saying one of the above, and you use IIS, you simply need to purchase this product, and run it to correct the problem. If your security scanning vendor is saying something else please Contact Us and we will let you know if we can help.